Technical Details
What is CHERIoT?
CHERIoT (Capability Hardware Extension to RISC-V for Internet of Things) is a technology that allows existing software to be executed on hardware which limits the effect of a large class of security vulnerabilities resulting from unsafe memory operations through the use of "capabilities".
CHERIoT was developed by Microsoft based on the CHERI work from the University of Cambridge. The CHERIoT Ibex core is an open source reference implementation of CHERIoT developed by Microsoft based on lowRISC's Ibex core.
How CHERI and CHERIoT work
Capability Hardware Enhanced RISC Instructions (CHERI) extend pointers with additional metadata to form capabilities. Capabilities include information such as memory bounds and access permissions which enables hardware to enforce fine-grained memory protection and compartmentalisation. To distinguish between capabilities and regular data, CHERI introduces an out-of-band tag bit that is cleared whenever an illegal operation is performed on a capability. This hardware based solution means existing codebases which are written in memory-unsafe languages (e.g. C and C++) don't have to be rewritten in modern memory-safe languages (e.g. Rust).
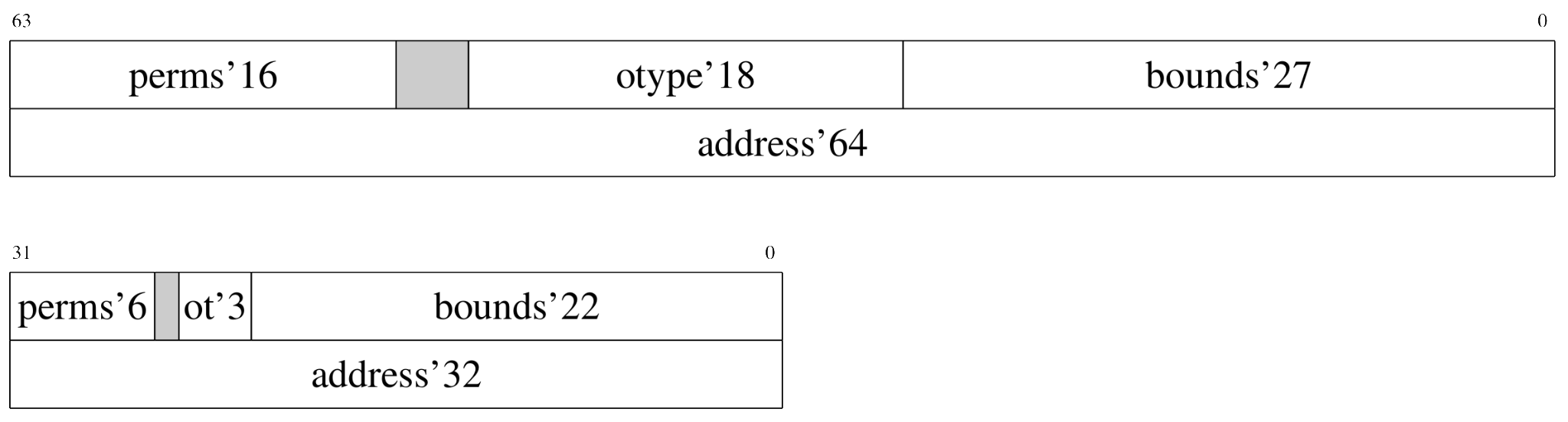
Capability Hardware Extension to RISC-V for Internet of Things (CHERIoT) draws from CHERI to create an RISC-V 32 ISA extension that brings these hardware abilities to systems with under 256 KiB of SRAM in a lightweight manner.
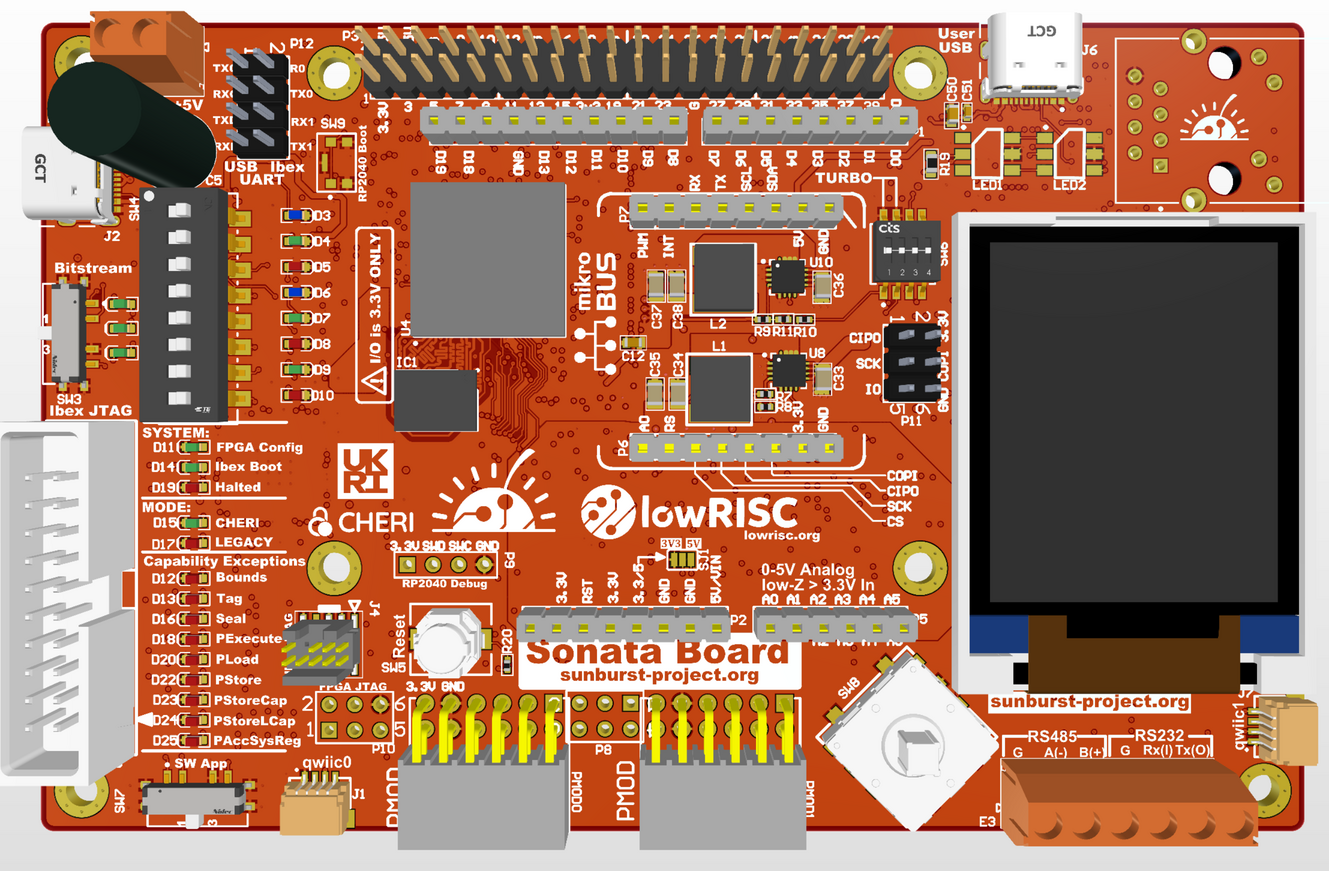
Sonata - Low Cost Development Board
The Sonata Board is a low cost development board with an FPGA which is able to host a small system comprised of the CHERIoT enabled Ibex and a number of peripherals, such as I2C and SPI. This system will be similar to the existing Ibex Demo System but with more peripherals and CHERIoT. Please find more technical details in the Sonata documentation and the Sonata repository.
Symphony - Extended Evaluation Development Board
A second, larger system will be developed that combines CHERIoT Ibex with an integrated OpenTitan design. This Symphony board is a more realistic system in which OpenTitan is used to provide security services like secure boot. The intent is for this to give developers a platform to experiment and design solutions that incorporate security-by-design extensions. Please find more technical details in the Symphony documentation the Symphony repository.

